request approval impact assessment build test monitor implemen|How Organizations Implement IT Change Requests : discount store It is crucial to take a multi-step approach instead of making large and unplanned sweeping changes. This will require you to identify and outline specific steps. These include measurable objectives, incentives, .
WEB26 de ago. de 2022 · Qual é o nome verdadeiro da julia minegirl. Ana; Julia; Juliana; Laura; Eles são um(a) Família; Conhecidos; Amigos; Que dia a julia minegirl faz .
{plog:ftitle_list}
Resultado da 25 de jan. de 2024 · FanDuel Casino Bonus Code; Hard Rock Casino Bonus Code; Borgata Bonus Code; Golden Nugget Bonus Code; Sportsbook Bonus Codes. See All; bet365 Bonus Code; . However, what we can say is that there have been cases of casino cheats using various devices to cheat at .
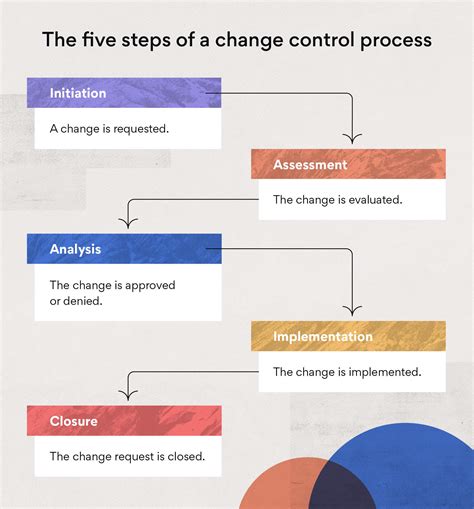
Request, impact assessment, approval, build/test, implement, monitor True or False? The process of remediation makes sure all personnel are aware of and comply with an organization's policies.Study with Quizlet and memorize flashcards containing terms like Authorizing official (AO), Separation of duties, Compartmentalized and more.Request, impact assessment, approval, build/test, implement, monitor. The term "data owner" refers to the person or group that manages an IT infrastructure.Answer. 5 months ago. The correct order of steps in the change control process is: Request. Impact Assessment. Approval. Build/Test. Implement. Monitor. So, the correct option is: Request, Continue reading. Discover more from: Cyber Foundations CYB200. Southern New Hampshire University. 730 Documents. Go to course.
Build / Test Once the change request is approved, the company builds and tests the change in a controlled environment to ensure it works as intended and does not adversely affect the system. This may include coding, . It is crucial to take a multi-step approach instead of making large and unplanned sweeping changes. This will require you to identify and outline specific steps. These include measurable objectives, incentives, .
Logging activities should differentiate among pipeline activities (infrastructure), pipeline consumers (developers) and systematic pipeline components (build creation and test tools). Additionally, alerts should be .4. Request, impact assessment, approval, build / test, monitor, implement. Here’s the best way to solve it. Solution. Share. 1. Request, approval, impact assessment, build/tes. View the full answer. Previous question Next question. Not the question you’re looking for? Post any question and get expert help quickly. Start learning.Request, impact assessment, approval, build/test, implement, monitor True or False? Using the names of superiors to convince another person that a higher authority has allowed access to information is a form of social engineering.How organizations manage implementation and post-implementation often makes all the difference. Mitigating risk during build, testing, and staging. Though every step in the IT change management process should help regulate and reduce .
Study with Quizlet and memorize flashcards containing terms like Okoye is identifying the set of privileges that should be assigned to a new employee in her organization. Which phase of the access control process is she performing? a. Identification b. Authentication c. Accountability d. Authorization, Everett is considering outsourcing security functions to a third-party service .
What is the correct order of steps in the change control process
Test. Expert Solutions. Q-Chat. Live. Blast. . Request, Impact assessment, Approval, Build/Test, Implement, monitor. See an expert-written answer! We have an expert-written solution to this problem! . Monitoring. Which intrusion detections system strategy relies on pattern matching?Question: 32 > 6 H 9 H Question 4 (2 points) Listen What is the correct order of steps in the change control process? Request, approval, impact assessment, build/test, monitor, implement Request, impact assessment, approval, build/test, implement, monitor Request, approval, impact assessment, build/test, implement, monitor Request, impact .Question: What is the correct order of steps in the change control process? 1. Request, approval, impact assessment, build/test, monitor, implement 2. View Test prep - Quiz6.docx from CIS CIS2350 at Daytona State College. 10 / 10 points What is the correct order of steps in the change control process? Request, approval, impact assessment, AI Chat with PDF
Cross-site request forgery (XSRF) . Request, impact assessment, approval, build/test, implement, monitor. See an expert-written answer! . In an accreditation process, who has the authority to approve a system for implementation? Authorizing official (AO) See .
request, impact assessment, approval, build/test, implement, monitor True or False? An American Institute of Certified Public Accountants (AICPA) Service Organization Control (SOC) 3 report is intended for public consumption.
The correct order of steps in the change control process is: Request, Impact Assessment, Approval, Build/Test, Implement, and finally Monitor. This method ensures that any changes being made are thoroughly assessed for their impact, approved by the right authorities, tested before implementation, and monitored regularly to verify success or to .
What Is The Correct Order Of Steps In The Change
Speeding Up Software Delivery With Effective Change
Solved What is the correct order of steps in the change
Monitor Therefore, the correct order is **Option B: Request, impact assessment, approval, build/test, implement, monitor.** --- **Question 2: Data Destruction Methods** When disposing of magnetic media and wishing to destroy the data stored on it, it is essential to choose the appropriate method for data destruction.Request, approval, impact assessment, build/test, monitor, implement. Request, impact assessment, approval, build/test, implement, monitor. . Request, impact assessment, approval, build/test, monitor, implement. Don't know? 14 of 20. Term. True or False? An American Institute of Certified Public Accountants (AICPA) Service Organization .
Percent Test Review Pt 2. Teacher 12 terms. MichellePotts8094. Preview. parent functions. 8 terms. . Certification is the formal agreement by an authorizing official to accept the risk of implementing a system. False. Procedures do NOT reduce mistakes in a crisis. . Request, impact assessment, approval, build/test, implement, monitor .
What is the correct order of steps in the change control process? A) Request, approval, impact assessment, build/test, monitor, implement B) Request, impact assessment, approval, build/test, implement, monitor C) Request, approval, impact assessment,.
Quiz yourself with questions and answers for Info Assurance - Quiz 9, so you can be ready for test day. Explore quizzes and practice tests created by teachers and students or create one from your course material.Ch1 and 9; Ch13 and 15; Ch3,4, and 11; Ch6; Ch8 and 12; Ch7; Ch2 and 5; Ch10; Learn with flashcards, games, and more — for free.O A Request, impact assessment, approval, build/test, monitor, implement B. Request approval Impact assessment, build/test, implement, monitor Request approval impact assessment, build/test, monitor, implement O D. Request, Impact assessment, approval, build/test, Implement monitor Which of the following is a digital forensics specialist least .
Certification is the formal agreement by an authorizing official to accept the risk of implementing. List the steps in a change request process Question 4 0 / 10 points Mandatory vacations minimize risk by rotating employees among . View Test prep - Quiz Chapter 7.pdf from ITI 432 at Rutgers University. Quiz Chapter 7.Request, impact assessment, approval, build/test, implement, monitor - pg 202 The term "data owner" refers to the person or group that manages an IT infrastructure. False - The Answer is system ownersTrue False QUESTION 2 Written security policies document management's goals and objectives. True False QUESTION 3 Certification is the formal agreement by an authorizing official to accept the risk of implementing a system. True False QUESTION 4 With proactive change management, management initiates the change to achieve a desired goal.
Chapter 9 Quiz quiz for Professional Development. Find other quizzes for Computers and more on Quizizz for free!
Request, impact assessment, approval, build/test, monitor, implement Question 25 (1 point) Bob is preparing to dispose of magnetic media and wishes to destroy the data stored on it.Study with Quizlet and memorize flashcards containing terms like Authorization, Access to a high level of expertise, Service Level Agreement (SLA) and more.
dr meter md 812 digital wood moisture meter
-Request, approval, impact assessment, build/test, monitor, implement -Request, impact assessment, approval, build/test, implement, monitor -Request, approval, impact .
What is the correct order of steps in the change control process? -Request, approval, impact assessment, build/test, monitor, implement -Request, impact assessment .2 / Which of the following is NOT an advantage to undertaking self-study of information security topics? Question options: Self-motivation. Flexible materialsA. Request, approval, impact assessment, build/test, monitor, implement B. Request, impact assessment, approval, build/test, implement, monitor C. Request, approval . test prep. Final Project 1.docx. Solutions Available. Liberty University. BMIS 570. test prep. . QUESTION 25 In an accreditation process, who has the authority to approve a system for implementation? O A. System owner O B. Certifier O C. System administrator O D. Authorizing . assessment. DERECHO DEL TRANSPORTE - T.8 (1).docx. Caso Sony.docx.
QUESTION 6 1. Karen is designing a process for issuing checks and decides that one group of users will have the authority to create new payees in the system while a separate group of users will have the authority to issue checks to those payees. The intent of this control is to prevent fraud. Which principle is Karen enforcing?
dr meter md-812 digital wood moisture meter
Resultado da Central de Atendimento: [email protected] – (98) 3303-3000. Título de Capitalização da Modalidade Filantropia Premiável de Contribuição Única emitido pela CAPEMISA Capitalização S/A, CNPJ 14.056.028/0001-55, aprovado pelo Processo SUSEP que consta no título. CONTATO LOCAL: .
request approval impact assessment build test monitor implemen|How Organizations Implement IT Change Requests